Spies, hackers, and reactors - a true story
March 24, 2022: The Department of Justice unseals two indictments that reveal a five-year saga of international spying and multi-phased hacking attacks, perpetrated by officers of Russia’s Federal Security Service (FSB).
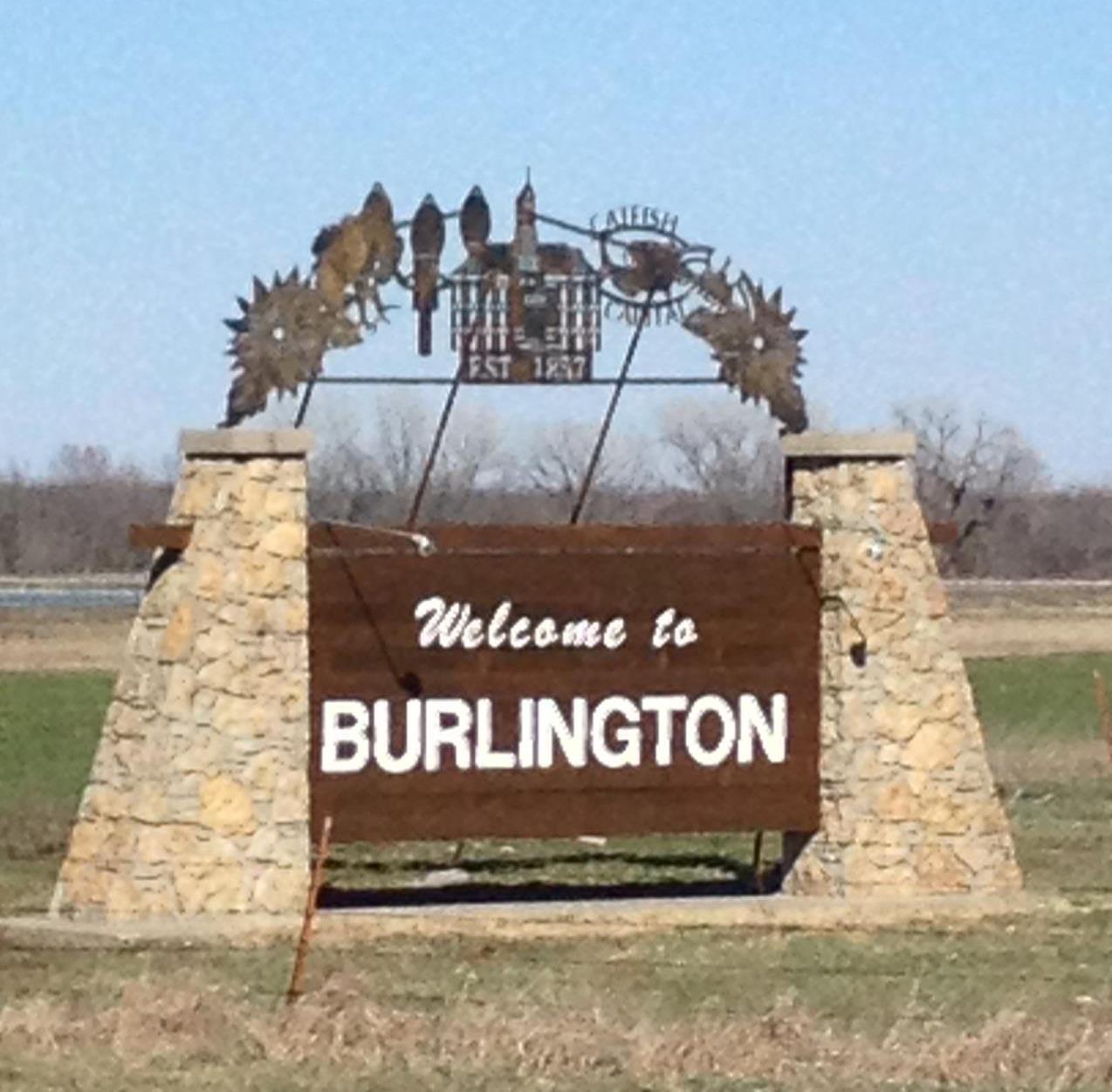
One, filed August 26, 2021, by a federal grand jury in Kansas City, Kansas, details an attack where, although the targets in whole were spread over 135 different countries, one of the main focuses was Burlington, Kansas.
Tiny Burlington, with a population of about 2500 people,
whose location on the Neosho River once made it "Catfish Capital of the World" -
and home to the Wolf Creek Nuclear Power Plant.
The Department of Justice press release reads like a spy novel:
United States v. Pavel Aleksandrovich Akulov, Mikhail Mikhailovich Gavrilov, and Marat Valeryevich Tyukov – defendants undertook years-long effort to target and compromise computer systems of energy sector companies
The FSB hackers, Pavel Aleksandrovich Akulov (Павел Александрович Акулов), 36, Mikhail Mikhailovich Gavrilov (Михаил Михайлович Гаврилов), 42, and Marat Valeryevich Tyukov (Марат Валерьевич Тюков), 39, were members of a Center 16 operational unit known among cybersecurity researchers as “Dragonfly,” “Berzerk Bear,” “Energetic Bear,” and “Crouching Yeti.” The indictment alleges that, between 2012 and 2017, Akulov, Gavrilov, Tyukov and their co-conspirators, engaged in computer intrusions, including supply chain attacks, in furtherance of the Russian government’s efforts to maintain surreptitious, unauthorized and persistent access to the computer networks of companies and organizations in the international energy sector, including oil and gas firms, nuclear power plants, and utility and power transmission companies. Specifically, the conspirators targeted the software and hardware that controls equipment in power generation facilities, known as ICS or Supervisory Control and Data Acquisition (SCADA) systems. Access to such systems would have provided the Russian government the ability to, among other things, disrupt and damage such computer systems at a future time of its choosing.
Despite the terrifying thought of a nuclear plant being at all hackable, this indictment sheds a lot of light on the threat actors, how they operate, and what they want. Knowing what happened is the first step in keeping it from happening again. So, how did they do it?
According to the indictment, the energy sector campaign had two phases. The first phase, between 2012 and 2014, was primarily a supply chain attack, where they hacked the computer networks of control system manufacturers and software providers, and then hid malware, known as Havex, inside legitimate software updates for those systems. After unsuspecting customers installed these updates, Havex allowed the actor to install additional malware and extract data, such as information about devices and resources on the network, lists of files and installed programs, e-mail address books, and virtual private network (VPN) configuration files.
Once they had a solid foothold in the networks of power and energy companies, it was time for phase 2: "Dragonfly 2.0." Running between 2014 and 2017, the agents changed tactics to more focused and personalized attacks towards specific locations and the engineers that work on the ICS/SCADA systems. Per the DOJ press release:
As alleged in the indictment, the conspirators’ tactics included spearphishing attacks targeting more than 3,300 users at more than 500 U.S. and international companies and entities, in addition to U.S. government agencies such as the Nuclear Regulatory Commission. In some cases, the spearphishing attacks were successful, including in the compromise of the business network (i.e., involving computers not directly connected to ICS/SCADA equipment) of the Wolf Creek Nuclear Operating Corporation (Wolf Creek) in Burlington, Kansas, which operates a nuclear power plant. Moreover, after establishing an illegal foothold in a particular network, the conspirators typically used that foothold to penetrate further into the network by obtaining access to other computers and networks at the victim entity.
During Dragonfly 2.0, the conspirators also began a "watering hole" attack. Here, they began by identifying several websites frequented by the engineers, and hacking the servers that host the sites. Once compromised, the websites would distribute malware onto the computers of the visiting engineers, capturing login credentials and other information.
That was a lot of work to put in, over a lot of time - what was the hoped for result? In the case of Wolf Creek and other nuclear reactors, outside entities should not be able to force a meltdown. According to the American Nuclear Society, "Nuclear facilities’ safety and control systems are, as a matter of course, not connected to business networks or the Internet." What they could do, though, is form a map of energy sector networks and equipment, and learn the best ways to damage or disrupt the power grid as possible, at will.
“The potential of cyberattacks to disrupt, if not paralyze, the delivery of critical energy services to hospitals, homes, businesses and other locations essential to sustaining our communities is a reality in today’s world,” said U.S. Attorney Duston Slinkard for the District of Kansas. “We must acknowledge there are individuals actively seeking to wreak havoc on our nation’s vital infrastructure system, and we must remain vigilant in our effort to thwart such attacks.”
What is the takeaway from all this, especially for those that aren't in the energy sector? The tools employed here, especially spearphishing, are a serious problem that can be leveraged on anyone. (Not sure what spearphishing is? Our own Dave and Bill explain it in this video.) We recommend starting your line of defense with phishing filters and employee training on spotting malicious email, as well as robust Managed Anti-Virus protections, all of which Soteria can help with..
More information and guidance can be found at The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) Shields Up program. CISA has tips and recommendations for organizations of any size, corporate leaders, and individuals. If you are curious, you can even take a deep dive into Technical Alerts, Bulletins, and Malware Analysis Reports regarding these and other malign cyber activities. Shields Up is located at:
https://www.cisa.gov/shields-up.
NEED HELP?
Talk to us:
NEED HELP? Talk to us:
NEED HELP?
Talk to us:
All Rights Reserved | Soteria, LLC
People Served. Problems Solved.
People Served. Problems Solved.
All Rights Reserved | Soteria, LLC